Cybersecurity frameworks provide a structure for managing cybersecurity risk. Companies in financial services, healthcare, and government verticals are required to adopt one or more cybersecurity frameworks and comply with requirements based on a variety of governments’ regulations (see the list at the end of this post). Many of our clients must comply with one or more standards. More of our clients have voluntarily adopted cybersecurity frameworks to manage risk associated with threats such as ransomware, phishing, malware, confidentiality, integrity, availability, state-sponsored attacks, and more. Ten Mile Square works with our clients to successfully adopt a framework and manage cyber risks with a set of controls tailored to each client’s organizational structure, legal and financial obligations, and employee skill sets. 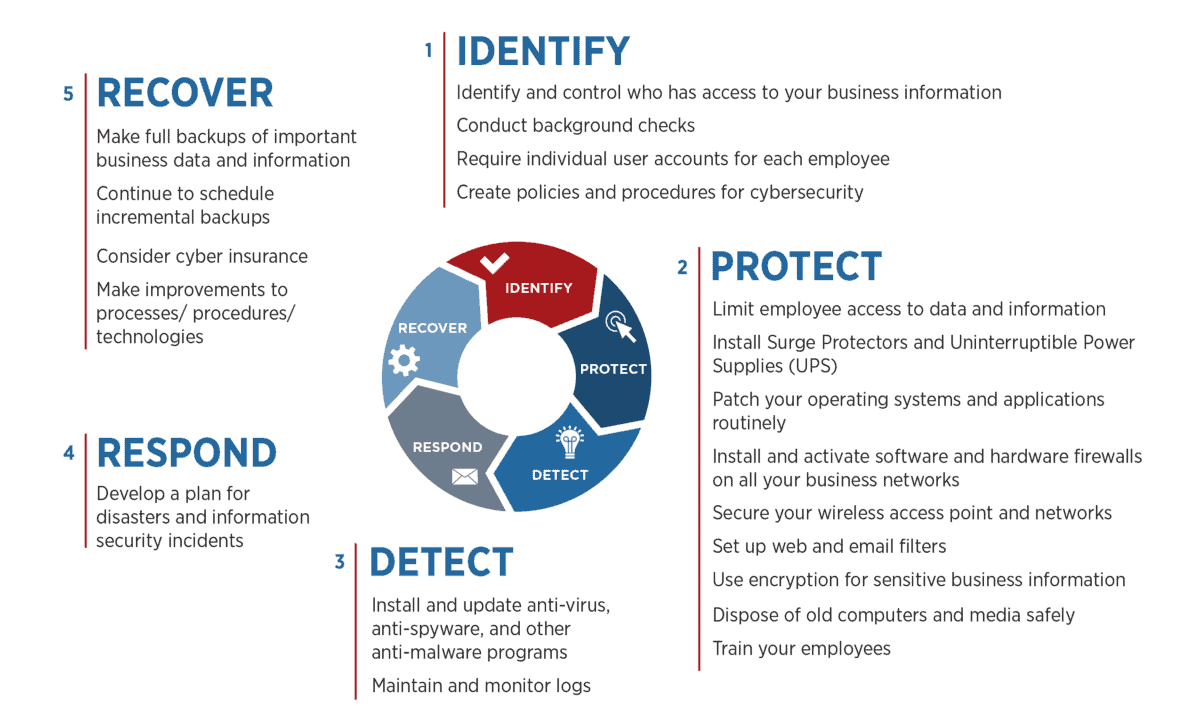
Cybersecurity Frameworks
Cybersecurity frameworks (CSF) provide an approach, structure, document definitions, and processes that drive the initiation activities and desired outcomes of a cybersecurity program. Each cybersecurity framework comes with a controls catalog that provides the context for dealing with specific risks. Some example frameworks include:
- NIST CSF – The NIST CSF is driven by US Government requirements, but it is also quite applicable to commercial usage. The NIST controls catalog is organized as 20 control families each composed of individual controls and control enhancement. There is enough detail for an organization to determine how they will enforce a specific control.
- CIS CSF – The CIS CSF is frequently adopted by commercial companies. It is control-driven like the NIST CSF. It also offers CIS Benchmarks that are collections of best practices for configuring specific technology assets like AWS, GCP, Linux, Docker, Kubernetes, Microsoft Azure, Microsoft Windows Server, databases, VMWare, and more.
- HITRUST CSF – HITRUST CSF is focused on HIPAA compliance for companies working with private health information (PHI).
These frameworks are symmetric and the control catalogs provide crosswalks to other frameworks and the requirements they seek to meet. Each control catalog further breaks down to tiers of implementation based on risk impact levels and maturity level of an organization.
Data Sensitivity
Understanding the data sensitivity in your systems is key to understanding your data risk. NIST CSF categorizes data sensitivity across security objectives and security impact levels. The security objectives are:
- Confidentiality – Preserving authorized restrictions on information access and disclosure, including means for protecting personal privacy and proprietary information.
- Integrity – Guarding against improper information modification or destruction, and includes ensuring information non-repudiation and authenticity.
- Availability – Ensuring timely and reliable access to and use of information.
The security impact levels are a measure of the effect that the loss of confidentiality, integrity, or availability would have:
- Low – Limited adverse effect
- Medium – Serious adverse effect
- High – Severe or catastrophic effect
The security impact level of a system is the high-water mark of the security impact levels. If the confidentiality security impact level is Low, the integrity security impact level is High, and the availability security impact level is Medium then the security impact level for the system is High.
System Boundaries
System boundaries are a key enabling concept for limiting the blast radius of a security incident. At the highest level, a system boundary is the logical boundary of what a system owner has financial and fiduciary responsibility for. In practice, a CISO should further partition an organization’s systems based on data sensitivity and security impact level. System boundaries can be between systems and between production systems and lower environments that support pre-production, testing, and development. For example, a system’s production and pre-production environments may have sensitive information, while testing could have de-identified data, and development may have synthetic data. The impact levels for production and pre-production could be high, testing medium, and development low.
Controls
The controls catalog represents the bridge from the cybersecurity requirements to the specification of how the requirements are met. Each line item details the methods that are used and any compensating controls that are used to reduce risk. Controls can be differentiated within a system boundary based on the security impact level. For example, a system’s production environment with sensitive data may have very restrictive controls about access and auditing. While the development environment with no sensitive data may have fewer required controls due to the absence of sensitive data. This avoids the one-size-fits-all issue of enforcing least privilege and other controls in a development environment. The goal is to leverage a collection of controls, process and technical, to reduce residual risk to a minimum.
Key Processes
There are additional key processes that cybersecurity frameworks address:
- Privacy plan
- Incident response plan
- Issues management plan
- Configuration management plan
- Records management plan
- Security training plan
- Compliance
- and others
We Can Work With You
Ten Mile Square can work with you to adopt and manage cyber risk using cybersecurity frameworks. Contact us at info@tenmilesquare.com.