
Wildcards Gone Bad: Why You Should Worry about TLS Certifications for Your Domains
Massive system breaches seem to be a common headline in the news today. Reading between the lines, you can hear
The implementation of security frameworks, controls, processes, and systems to safeguard data and privacy information. Protect your systems against security threats, respond to all vulnerabilities, and implement security compliance through the infrastructure level.

Massive system breaches seem to be a common headline in the news today. Reading between the lines, you can hear

Why would you do this? Normally, to access Amazon Web Services (AWS) from the command line (AWS CLI), SDKs, or

In healthtech organizations, leaders need to make careful decisions around acceptable cybersecurity risk management when using Protected Health Information (PHI).

Ransomware is a serious threat to business continuity for healthtech and healthcare companies and compliance with the HIPAA Security Rule.
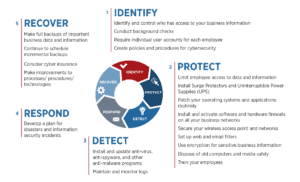
Cybersecurity frameworks provide a structure for managing cybersecurity risk. Companies in financial services, healthcare, and government verticals are required to
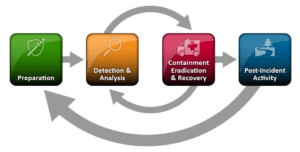
Preparing your business to protect against and be ready to respond to security incidents reduces your company’s risk. The business
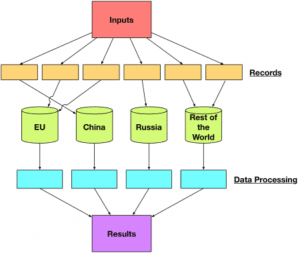
By now you’ve read numerous articles about how the European Union (EU) will enforce its General Data Protection Regulation (GDPR).