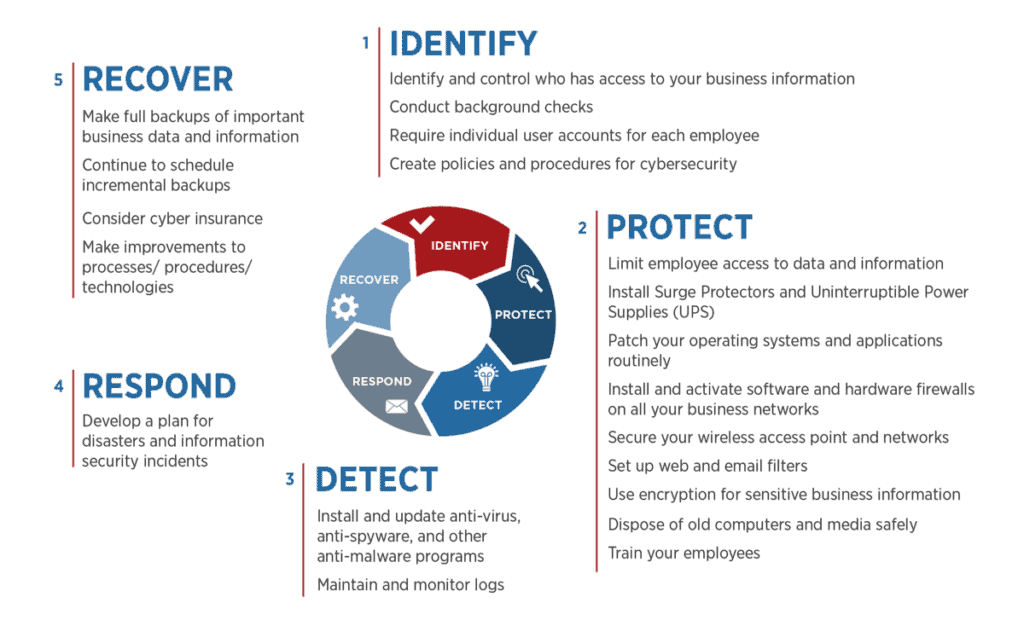
Preparing your business to protect against and be ready to respond to security incidents reduces your company’s risk. The business leadership has responsibilities that they must address to enable the technology team’s defense and response.
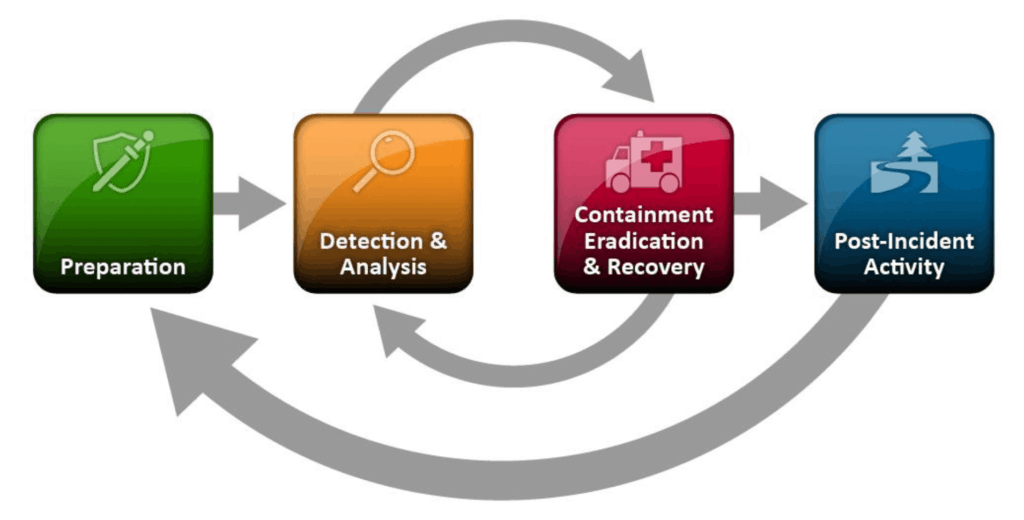
Here are 7 questions you need to answer:
- What is a security incident? You need to concisely define what constitutes an incident. e.g. an occurrence that jeopardizes the integrity, confidentiality, or availability of an information system or its information, or an unauthorized disclosure of sensitive information.
- What is sensitive information? It depends on your business, but business records, financial, client, employee, intellectual property (IP) or other information for which loss, misuse, unauthorized access, or modification could endanger the business, employees, clients, individuals, or others, including PII, PHI, or PCI (you need to know what this is!).
- PII – Personally identifiable information is anything that can be used to identify a particular person – name, email, phone number, address, social security number, driver’s license number, etc.
- PHI – Protected health information is individually identifiable information relating to the past, present, or future health status of an individual. PHI is protected under the Health Insurance Portability and Accountability Act of 1996 (HIPPA).
- PCI – Payment card industry data security standard (PCI DSS) for cardholder data. If you accept payment cards then you must comply with the PCI DSS.
- What kinds of incidents can we have? Categorizing incidents aids in focusing the response process, e.g. intrusion, ransomware, privacy breach, intellectual property breach.
- How do we rank the severity of an incident? Severity is your guide to the degree of risk and scale of response. e.g. a low severity incident could be one where publicly available information was breached.
- What is our incident response policy? The policy lays out why, what, who and when of incident response.
- Who is responsible for our incident response plan and procedures? Who is responsible for how incidents will be handled as well as the process and procedures.
- What is our notification and communication plan and procedures? Internal communication paths must be defined. Communication outside the company may be with law enforcement, media, and those impacted by the breach; there may be statutory timelines and disclosure requirements.
With the advent of GDPR, the EU’s General Data Protection Regulation, businesses operating in the EU have specific compliance responsibilities. GDPR paved the way for the CCPA, the California Consumer Privacy Act, and impacts business operating in California. CCPA goes into effect on January 1, 2020.
NIST, the National Institute for Standards and Technology, publishes a helpful guide – “NIST 800-61 rev. 2 – Computer Security Incident Handling Guide.”