Cybersecurity
Want to get ahead or simply understand your cybersecurity and compliance standards, requirements, or policies?
When it comes to cybersecurity, you want to be proactive rather than reactive. If security policies and controls are not made into standard operating procedures (SOPs) that cover your product development process, chances are high that your software releases will be slower to market and making changes will be more challenging than they need to be.
Ten Mile Square helps you comply with standards in ways that won’t disrupt your business. We work with you to build security policies into a framework that implements security compliance starting at the infrastructure level. We can then turn product features into a roadmap supported by a cybersecurity framework for a more streamlined product lifecycle that is compliant with your security standards and requirements. Take security seriously and let our consultants help you figure out the best solution for your specific needs, such as:
- Develop recommendations for a secure cloud infrastructure
- Solve data management and compliance requirements, including GDPR, SOC 2, HIPAA, FedRAMP, FISMA, CCPA, and more
- Customize a solution to clean up information security
- Mitigating risk using a quantitative prediction of data breach and exfiltration likelihood
HEALTHTECH SECURITY
“We had a great product but had holes in our SaaS architecture and security. Ten Mile Square came in to conduct a technology assessment and quickly laid out a plan, executed the strategy, and provided us the resources we needed. Serving as our fractional CTO, Frank understood our business and growth goals. He provided the foresight of what we needed to meet our company’s technology vision.”
– ADAM GROSS, CEO, RIGHTEYE
Securing this Healthtech’s AWS Infrastructure

- Significantly reduced escaped defects in product releases
- Stabilized engineering resources by embedding with their team as a fractional CTO
- Secured the company’s AWS infrastructure and addressed compliance requirements for hospital and Department of Defense customers
Securing the DAM Cloud Architecture

CLOUD SECURITY
- Secured its cloud architecture to meet requirements for its large brand name customers
- Defined the architecture around the management and security benefits offered by the cloud
- Identified points where the cloud deployment is interconnected to traditional data environments running legacy code
Featured Cybersecurity Articles

Is Cybersecurity Risk Management Slowing Down Innovation and Speed to Market?
In healthtech organizations, leaders need to make careful decisions around acceptable cybersecurity risk management when using Protected Health Information (PHI).

Preventing Ransomware and Protecting ePHI with Zero Trust and Microsegmentation
Ransomware is a serious threat to business continuity for healthtech and healthcare companies and compliance with the HIPAA Security Rule.
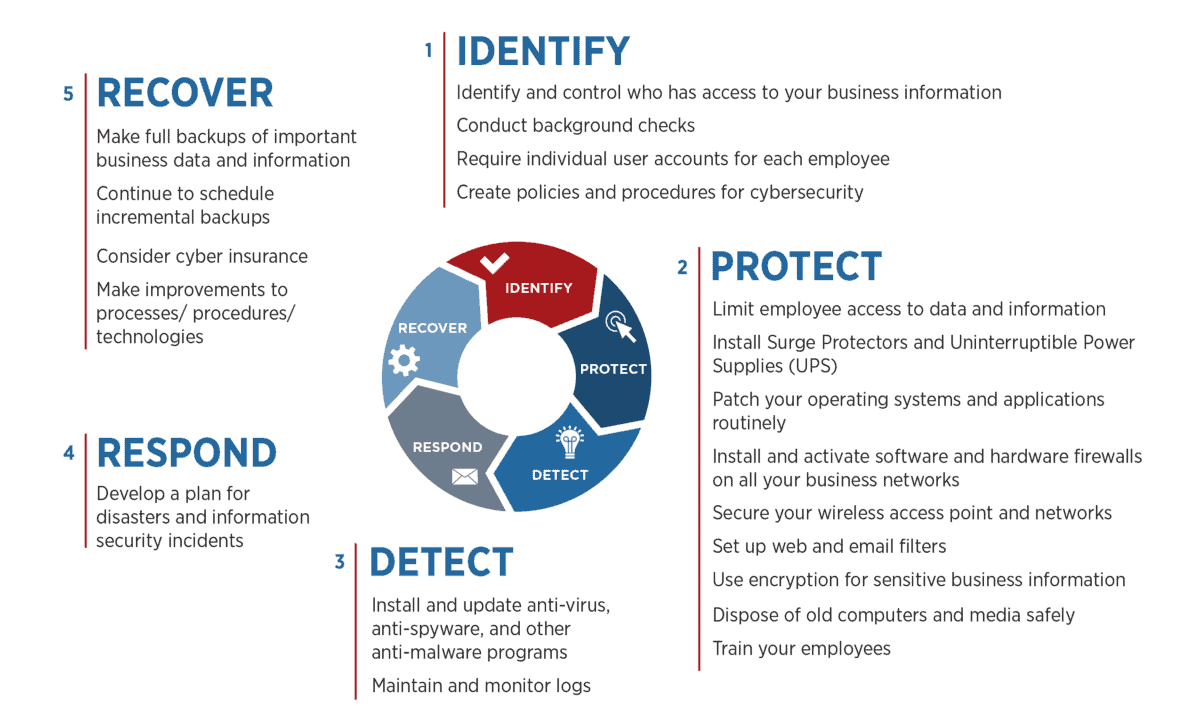
Cybersecurity Frameworks to Manage Cyber Risk
Cybersecurity frameworks provide a structure for managing cybersecurity risk. Companies in financial services, healthcare, and government verticals are required to
Security Checklist
- Is your company having trouble prioritizing standards adoption?
- Having trouble understanding the list of compliance standards?
- Is security compliance not seen as an important part of product development in your organization?
- Is adherence to standards slowing down your new product releases?
- Worried about being sued or getting an injunction brought against you for compliance failure?